Раздел: Документация
0 1 2 3 4 5 6 7 ... 117  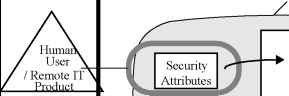 Target of Evaluation (TOE) TOE Security Functions Interface (TSFI) Subject Subject TOE Security Functions (TSF) Enforces TOE Security Policy w (TSP) -r-- 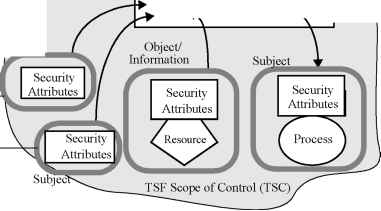 Figure 1.1 - Security functional requirements paradigm (Monolithic TOE) This part of ISO/IEC 15408 is a catalogue of security functional requirements that can be specified for a Target of Evaluation (TOE). A TOE is an IT product or system (along with user and administrator guidance documentation) containing resources such as electronic storage media (e.g. disks), peripheral devices (e.g. printers), and computing capacity (e.g. CPU time) that can be used for processing and storing information and is the subject of an evaluation. TOE evaluation is concerned primarily with ensuring that a defined TOE Security Policy (TSP) is enforced over the TOE resources. The TSP defines the rules by which the TOE governs access to its resources, and thus all information and services controlled by the TOE. The TSP is, in turn, made up of multiple Security Function Policies (SFPs). Each SFP has a scope of control, that defines the subjects, objects, and operations controlled under the SFP. The SFP is implemented by a Security Function (SF), whose mechanisms enforce the policy and provide necessary capabilities. Local User V3 Local (Internal TOE) Trusted Path . Internal TOE Transfer SF SF SF SF SF SF  Transfers V... Outside TSF Control  Local TOE .Inter-TSF Transfer Inter-TSF Trusted Path / Untrusted IT Product RF: Remote Function i-IRemote Trusted IT Product Remote User Figure 1.2 - Diagram of security functions in a distributed TOE Those portions of a TOE that must be relied on for the correct enforcement of the TSP are collectively referred to as the TOE Security Functions (TSF). The TSF consists of all hardware, software, and firmware of a TOE that is either directly or indirectly relied upon for security enforcement. A reference monitor is an abstract machine that enforces the access control policies of a TOE. A reference validation mechanism is an implementation of the reference monitor concept that possesses the following properties: tamperproof, always invoked, and simple enough to be subjected to thorough analysis and testing. The TSF may consist of a reference validation mechanism and/or other security functions necessary for the operation of the TOE. The TOE may be a monolithic product containing hardware, firmware, and software. Alternatively a TOE may be a distributed product that consists internally of multiple separated parts. Each of these parts of the TOE provides a particular service for the TOE, and is connected to the other parts of the TOE through an internal communication channel. This channel can be as small as a processor bus, or may encompass a network internal to the TOE. When the TOE consists of multiple parts, each part of the TOE may have its own part of the TSF which exchanges user and TSF data over internal communication channels with other parts of the TSF. This interaction is called internal TOE transfer. In this case the separate parts of the TSF abstractly form the composite TSF, which enforces the TSP. TOE interfaces may be localised to the particular TOE, or they may allow interaction with other IT products over external communication channels. These external interactions with other IT products may take two forms: a)The security policy of the remote trusted IT product and the TSP of the local TOEs have been administratively coordinated and evaluated. Exchanges of information in this situation are called inter-TSF transfers, as they are between the TSFs of distinct trusted products. b)The remote IT product may not be evaluated, indicated in Figure 1.2 as untrusted IT product, therefore its security policy is unknown. Exchanges of information in this situation are called transfers outside TSF control, as there is no TSF (or its policy characteristics are unknown) on the remote IT product. The set of interactions that can occur with or within a TOE and are subject to the rules of the TSP is called the TSF Scope of Control (TSC). The TSC encompasses a defined set of interactions based on subjects, objects, and operations within the TOE, but it need not encompass all resources of a TOE. The set of interfaces, whether interactive (man-machine interface) or programmatic (application programming interface), through which resources are accessed that are mediated by the TSF, or information is obtained from the TSF, is referred to as the TSF Interface (TSFI). The TSFI defines the boundaries of the TOE functions that provide for the enforcement of the TSP. Users are outside of the TOE, and therefore outside of the TSC. However, in order to request that services be performed by the TOE, users interact with the TOE through the TSFI. There are two types of users of interest to the ISO/IEC 15408-2 security functional requirements: human users and external IT entities. Human users are further differentiated as local human users, meaning they interact directly with the TOE via TOE devices (e.g. workstations), or remote human users, meaning they interact indirectly with the TOE through another IT product. A period of interaction between users and the TSF is referred to as a user session. Establishment of user sessions can be controlled based on a variety of considerations, for example: user authentication, time of day, method of accessing the TOE, and number of allowed concurrent sessions per user. This part of ISO/IEC 15408 uses the term authorised to signify a user who possesses the rights and/or privileges necessary to perform an operation. The term authorised user, therefore, indicates that it is allowable for a user to perform an operation as defined by the TSP. To express requirements that call for the separation of administrator duties, the relevant ISO/IEC 15408-2 security functional components (from family FMT SMR) explicitly state that administrative roles are required. A role is a pre-defined set of rules establishing the allowed interactions between a user and the TOE. A TOE may support the definition of any number of roles. For example, roles related to the secure operation of a TOE may include "Audit Administrator" and "User Accounts Administrator". 0 1 2 3 4 5 6 7 ... 117
|
