Раздел: Документация
0 ... 2 3 4 5 6 7 8 ... 117 TOEs contain resources that may be used for the processing and storing of information. The primary goal of the TSF is the complete and correct enforcement of the TSP over the resources and information that the TOE controls. TOE resources can be structured and utilised in many different ways. However, ISO/IEC 15408-2 makes a specific distinction that allows for the specification of desired security properties. All entities that can be created from resources can be characterised in one of two ways. The entities may be active, meaning that they are the cause of actions that occur internal to the TOE and cause operations to be performed on information. Alternatively, the entities may be passive, meaning that they are either the container from which information originates or to which information is stored. Active entities are referred to as subjects. Several types of subjects may exist within a TOE: a)those acting on behalf of an authorised user and which are subject to all the rules of the TSP (e.g. UNIX processes); b)those acting as a specific functional process that may in turn act on behalf of multiple users (e.g. functions as might be found in client/server architectures); or c)those acting as part of the TOE itself (e.g. trusted processes). ISO/IEC 15408-2 addresses the enforcement of the TSP over types of subjects as those listed above. Passive entities (i.e. information containers) are referred to in the ISO/IEC 15408-2 security functional requirements as objects. Objects are the targets of operations that may be performed by subjects. In the case where a subject(an active entity) is the target of an operation (e.g. interprocess communication), a subject may also be acted on as an object. Objects can contain information. This concept is required to specify information flow control policies as addressed in the FDP class. Users, subjects, information and objects possess certain attributes that contain information that allows the TOE to behave correctly. Some attributes, such as file names, may be intended to be informational (i.e. to increase the user-friendliness of the TOE) while others, such as access control information, may exist specifically for the enforcement of the TSP. These latter attributes are generally referred to as security attributes. The word attribute will be used as a shorthand in this part of ISO/IEC 15408 for the word security attribute, unless otherwise indicated. However, no matter what the intended purpose of the attribute information, it may be necessary to have controls on attributes as dictated by the TSP. Data in a TOE is categorised as either user data or TSF data. Figure 1.3 depicts this relationship. User Data is information stored in TOE resources that can be operated upon by users in accordance with the TSP and upon which the TSF places no special meaning. For example, the contents of an electronic mail message is user data. TSF Data is information used by the TSF in making TSP decisions. TSF Data may be influenced by users if allowed by the TSP. Security attributes, authentication data and access control list entries are examples of TSF data. There are several SFPs that apply to data protection such as access control SFPs and information flow control SFPs. The mechanisms that implement access control SFPs base their policy decisions on attributes of the subjects, objects and operations within the scope of control. These attributes are used in the set of rules that govern operations that subjects may perform on objects. The mechanisms that implement information flow control SFPs base their policy decisions on the attributes of the subjects and information within the scope of control and the set of rules that govern the operations by subjects on information. The attributes of the information, which may be associated with the attributes of the container (or may not, as in the case of a multi-level database) stay with the information as it moves. 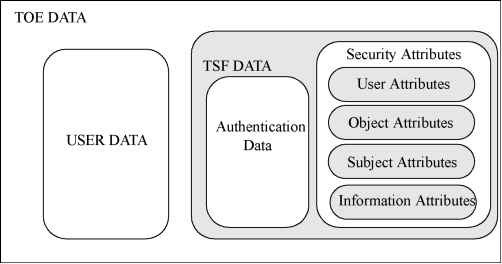 Figure 1.3 - Relationship between user data and TSF data Two specific types of TSF data addressed by ISO/IEC 15408-2 can be, but are not necessarily, the same. These are authentication data and secrets. Authentication data is used to verify the claimed identity of a user requesting services from a TOE. The most common form of authentication data is the password, which depends on being kept secret in order to be an effective security mechanism. However, not all forms of authentication data need to be kept secret. Biometric authentication devices (e.g. fingerprint readers, retinal scanners) do not rely on the fact that the data is kept secret, but rather that the data is something that only one user possesses and that cannot be forged. The term secrets, as used in ISO/IEC 15408-2 functional requirements, while applicable to authentication data, is intended to also be applicable to other types of data that must be kept secret in order to enforce a specific SFP. For example, a trusted channel mechanism that relies on cryptography to preserve the confidentiality of information being transmitted via the channel can only be as strong as the method used to keep the cryptographic keys secret from unauthorised disclosure. Therefore, some, but not all, authentication data needs to be kept secret and some, but not all, secrets are used as authentication data. Figure 1.4 shows this relationship between secrets and authentication data. In the Figure the types of data typically encountered in the authentication data and the secrets sections are indicated. 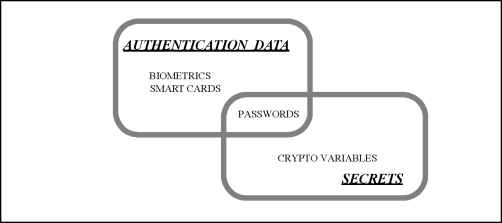 Figure 1.4 - Relationship between "authentication data" and "secrets" 0 ... 2 3 4 5 6 7 8 ... 117 |












