Раздел: Документация
0 ... 10 11 12 13 14 15 16 ... 20 5.5 Use of TOE evaluation results IT products and systems differ in respect to the use of the results of the evaluation. Figure 5.2 shows options for processing the results of evaluation. Products can be evaluated and catalogued at successively higher levels of aggregation until operational systems are achieved, at which time they may be subject to evaluation in connection with system accreditation. PPs Catalogue (optional) Evaluated Products Catalogue (optional) Security requirements  Evaluation results Evaluated product 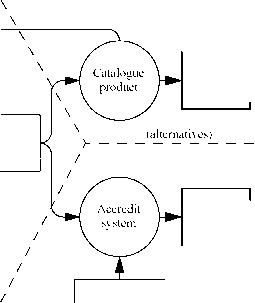 Accredited system System accreditation criteria Figure 5.2 - Use of TOE evaluation results The TOE is developed in response to requirements that may take account of the security properties of any evaluated products incorporated and PPs referenced. Subsequent evaluation of the TOE leads to a set of evaluation results documenting the findings of the evaluation. Following an evaluation of an IT product intended for wider use, a summary of the evaluation findings might be entered in a catalogue of evaluated products so that it becomes available to a wider market seeking to use secure IT products. Where the TOE is or will be included in an installed IT system that has been subject to evaluation, the evaluation results will be available to the system accreditor. The CC evaluation results may then be considered by the accreditor when applying organisation specific accreditation criteria that call for CC evaluation. CC evaluation results are one of the inputs to an accreditation process that leads to a decision on accepting the risk of system operation. Annex A (informative) The Common Criteria project A.1 Background to the Common Criteria project The CC represents the outcome of a series of efforts to develop criteria for evaluation of IT security that are broadly useful within the international community. In the early 1980s the Trusted Computer System Evaluation Criteria (TCSEC) was developed in the United States. In the succeeding decade, various countries began initiatives to develop evaluation criteria that built upon the concepts of the TCSEC but were more flexible and adaptable to the evolving nature of IT in general. In Europe, the Information Technology Security Evaluation Criteria (ITSEC) version 1.2 was published in 1991 by the European Commission after joint development by the nations of France, Germany, the Netherlands, and the United Kingdom. In Canada, the Canadian Trusted Computer Product Evaluation Criteria (CTCPEC) version 3.0 was published in early 1993 as a combination of the ITSEC and TCSEC approaches. In the United States, the draft Federal Criteria for Information Technology Security (FC) version 1.0 was also published in early 1993, as a second approach to combining North American and European concepts for evaluation criteria. Work had begun in 1990 in the International Organization for Standardization (ISO) to develop an international standard evaluation criteria for general use. The new criteria was to be responsive to the need for mutual recognition of standardised security evaluation results in a global IT market. This task was assigned to Working Group 3 (WG 3) of subcommittee 27 (SC 27) of the Joint Technical Committee 1 (JTC 1). Initially, progress was slow within WG3 because of the extensive amount of work and intensive multilateral negotiations required. A.2 Development of the Common Criteria In June 1993, the sponsoring organisations of the CTCPEC, FC, TCSEC and ITSEC (which are identified in the next subclause) pooled their efforts and began a joint activity to align their separate criteria into a single set of IT security criteria that could be widely used. This activity was named the CC Project. Its purpose was to resolve the conceptual and technical differences found in the source criteria and to deliver the results to ISO as a contribution to the international standard under development. Representatives of the sponsoring organisations formed CC Editorial Board (CCEB) to develop the CC. A liaison was then established between the CCEB and WG 3, and the CCEB contributed several early versions of the CC to WG 3 via the liaison channel. As a result of the interaction between WG 3 and the CCEB, these versions were adopted as successive working drafts of various Parts of the ISO criteria beginning in 1994. Version 1.0 of the CC was completed by the CCEB in January 1996 and was approved by ISO in April 1996 for distribution as a Committee Draft (CD). The CC Project then performed a number of trial evaluations using CC Version 1.0, and an extensive public review of the document was conducted. The CC Project subsequently undertook an extensive revision of the CC based on the comments received from trial use, public review and interaction with ISO. The revision work has been carried out by the successor to the CCEB, now called the CC Implementation Board (CCIB). The CCIB completed CC version 2.0 "Beta" in October 1997 and presented it to WG 3, which approved it as a Second Committee Draft. Subsequent intermediate draft versions were provided informally to WG 3 experts for feedback as they were produced by the CCIB. The CCIB received and responded to a series of comments that came both directly from WG 3 experts and from ISO National Bodies via the CD balloting. The culmination of this process is CC Version 2.0. For historical and continuity purposes, ISO/IEC JTC 1/SC 27/WG 3 has accepted the continued use of the term "Common Criteria" (CC) within the document, while recognising that its official name in the ISO context is "Evaluation Criteria for Information Technology Security". A.3 Common Criteria project sponsoring organisations The seven European and North American governmental organisations listed below constitute the CC project sponsoring organisations. These organisations have provided nearlyall of the effortthat went into developing the CC from its inception to its completion. These organisations are also "evaluation authorities" for their respective national governments. They have committed themselves to replacing their respective evaluation criteria with the CC version 2.0 now that its technical development has been completed and it is in the final stages of acceptance as an International Standard. CANADA: Communications Security Establishment Criteria Coordinator I2A Computer and Network Security P.O. Box 9703, Terminal Ottawa, Canada K1G 3Z4 Tel: +1.613.991.7882, Fax: +1.613.991.7455 E-mail: criteria@cse-cst.gc.ca WWW: http: www.cse-cst.gc.ca/cse/english/cc.html FTP: ftp: ftp.cse-cst.gc.ca/pub/criteria/CC2.0 GERMANY: Bundesamt fur Sicherheit in der Informationstechnik (BSI) German Information Security Agency (GISA) Abteilung V Postfach 20 03 63 D-53133 Bonn Germany Tel: +49.228.9582.300, Fax: +49.228.9582.427 E-mail: cc@bsi.de WWW: http: www.bsi.bund.de/cc FRANCE: Service Central de la Securite des Systemes dInformation (SCSSI) Centre de Certification de la Securite des Technologies de lInformation 18, rue du docteur Zamenhof F-92131 Issy les Moulineaux France Tel: +33.1.41463784, Fax: +33.1.41463701 E-mail: ssi20@calva.net NETHERLANDS: Netherlands National Communications Security Agency P.O. Box 20061 NL 2500 EB The Hague The Netherlands Tel: +31.70.3485637, Fax: +31.70.3486503 E-mail: criteria@nlncsa.minbuza.nl WWW: http: www.tno.nl/instit/fel/refs/cc.html 0 ... 10 11 12 13 14 15 16 ... 20 |












